Your comprehensive cyber security mitigation approach should include a firewall. Because you're not a large bank or Apple, your company is safe from hackers. Right? Unfortunately, the answer is no. Because SMEs are less likely to invest in cyber security, many hackers target small-to-medium firms.
So, how can you keep your company's and clients' confidential information out of the wrong hands? A firewall can contribute to your entire strategy by serving as a critical component of a company's data-security infrastructure.
What is a firewall, exactly?
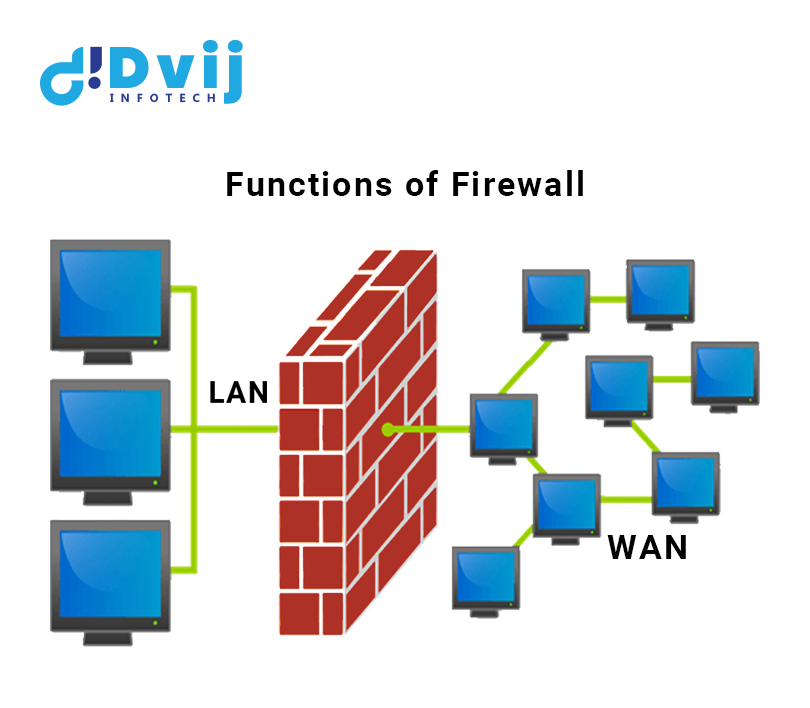
A firewall is a network security device that monitors and regulates incoming and outgoing traffic on a computer or corporate network. A set of regulations or guidelines underpins this control. These can be set up on the firewall itself or through the firewall administration console.
A firewall is a network security device that monitors and regulates incoming and outgoing traffic on a computer or corporate network. A set of regulations or guidelines underpins this control. These can be set up on the firewall itself or through the firewall administration console.
A firewall, in essence, aids in the protection and security of the devices, applications, and data that reside on the internal network behind it. This can happen at your workplace, between offices, or even between services hosted by your hosting provider or in the cloud.
A better-protected network is a result of installing a firewall on your network or in front of your cloud services. You're assisting in the protection of your network's users and data from malicious online attacks and vulnerabilities. To lower the danger of an attack and secure critical data, firewalls are an essential component of your cybersecurity system.
Most modern company requirements are too basic for early firewalls from the 1980s and 1990s (as well as the cheap firewalls marketed today). They only allow traffic through a specific port, website, or IP address. Because they use application-level scanning and machine learning, newer and more powerful firewalls go hundreds of steps further.
Functions of firewall are as follows:
Monitoring and controlling bandwidth
One of the best firewall functions is bandwidth control, often known as traffic shaping. We don't always have access to limitless bandwidth. As a result, it's critical to seize control of the bandwidth we do have. You can manage the bandwidth available to sites, programs, and users with a firewall.
Perhaps you'd like to increase the overall bandwidth available to your graphics department. You could also want to reduce the amount of bandwidth used by cloud-based file synchronization services. Popular services such as OneDrive, DropBox, and Google Drive can all cause major problems in this situation. The solution, of course, is not to cease utilizing these incredible programs. Instead, hello, bandwidth management!
You can allocate a defined amount of dedicated bandwidth for your VoIP phone system using bandwidth control on your firewall. You can even give priority to other cloud-based services like Skype for Business or Google Hangouts. This will assist to eliminate the terrible jitter that ruins any phone or video call.
You can choose when backups across sites take place so that they don't interfere with business operations. You can also give backups a huge piece of the connection when it's not in use. Another fantastic feature to use is forcing backup traffic to flow through cheaper networks. This means that when quality actually matters, more important traffic can be directed to your higher-quality connections.
Filtering of the internet
A web filter firewall is similar to a content filtering firewall. A web filter firewall is a software program that monitors the data packets sent and received by your computer. It filters any compromising content that has been blocked or identified in this way. These rules can be used to block access to any potentially dangerous or insecure websites. It can also be used to prohibit employees from accessing sites that could harm their productivity (like social networking websites).
The majority of firewalls allow you to restrict access to specific websites. This can be done on a case-by-case basis, or your firewall can include a subscription that allows you to select which categories you don't want others to see. Illicit activities, downloading illegal content, gambling, and a variety of other activities may be things you want to prohibit workers or visitors from doing on the business network.
Because these types of websites frequently change their IP addresses and domain names, the firewall vendor will keep their lists up to date for you. With their automatically updated lists, vendors like Cisco and Fortigate take the hassle out of this for you.
Don't be fooled by the ease with which some firewall filters can be downloaded from the internet.
These firewalls, in comparison to firewalls set up by IT specialists and paid firewall subscriptions from respected companies, do not provide adequate protection. Anyone who is familiar with firewalls may simply breach them.
Documentation
Having access to a firewall's logs gives you real-time information about what's going on in your network. The ability to display graphs in real-time and show you what vulnerabilities or assaults are occurring is one of the most desired firewall capabilities.
The data acquired by the firewall can be simplified and digested by combining the information documented by the firewall on the source address, source port, and destination address and port.
This information, which is logged by the firewall, can be used to identify any questionable connection attempt.
Firewall logging is extremely useful because it allows you to see if a new firewall is performing well (so you can debug if necessary); if malicious activity is taking place in your network; any failed login attempts from a specific IP address (so you can create a rule to block connections from this IP); and if someone is using your Using the system as a launching pad (such as launching attacked against your systems or networks).
SD-WAN and Internet aggregation
For enterprises that require several internet connections, link aggregation and SD-WAN (Software-defined Wide Area Network) are excellent features. They're particularly beneficial if you're connecting to numerous places, such as branch offices or cloud services, via multiple links.
A link integration interface is a collection of physical interfaces that can be configured to act as a single logical interface. Businesses utilize it to boost the combined data throughput so that capacity can be increased beyond that of a single physical interface. If a physical link fails, it can also be used to offer redundancy.
SD-WAN is a virtual WAN architecture that allows businesses to link apps and users securely using any mix of transport services. MPLS, LTE, and broadband internet services are all examples of this.
Redundancy is possible thanks to the capacity to employ several links. It also allows you to meet your bandwidth needs by combining many low-cost links from different suppliers.
Using a sandbox
Sandboxing is one of those crucial firewall functions that most users are unaware of. It takes a file or executable and opens it in a completely isolated and independent "test" environment as you download it.
This simulates the end-user environment outside of your production environment without endangering your users. After that, a sandbox opens the file, runs it, scans it, and looks for malware or suspicious activities.
It will pass the files or URL to the end-user if they appear to be secure. If the file or URL behaves maliciously, a new threat has been identified! Sandboxing is very good at protecting against zero-day attacks (those that haven't been seen before and don't match known malware signatures). It falls under the area of sophisticated threat security, which goes beyond the capabilities of ordinary inbound email filter scanners.
Sandboxing is an extra layer of security that ensures that if an email contains unfamiliar URL links, file kinds, or senders but still makes it past the email filter, tests are run before it reaches the network or mail server.
Wireless controller built-in
Using a firewall with a built-in wireless controller is a great way to save money and consolidate all of your policies and controls into one location or platform.
You have complete control over your environment by just setting up different SSIDs and regulations. The number of wireless access points you can use depends on the firewall model you choose. Low-cost devices will have two to ten access points, whereas higher-end models will have hundreds.
You can even use the same policies across all of your sites. This allows your users to move between sites without having to log in or enter passwords each time.
Packet Inspection (Deep Packet Inspection)
Deep packet inspection (DPI) is a fantastic capability that we can no longer live without. This is a more complex method of evaluating and regulating network traffic, in which the firewall examines each packet as it passes through. It can scan for hidden viruses and harmful behavior as it analyses the content of packets going through a checkpoint, making real-time choices based on rules set by the organization, ISP, or network manager. Following that, the firewall can decide what to do with the packet. It has the ability to either block the sender or drop the transmission. DPI has been able to do deeper and deeper inspections on massive amounts of traffic in real-time thanks to technological developments. This is why it is one of our favorite firewall features.
The best part of DPI is that if the firewall detects a new source threat, it will send a notification to the vendor. This will be examined, and other firewalls throughout the world will be upgraded as a result. What's the end result? Different networks work together to keep one another safe.