In today's hyper-connected world, the ability to rapidly and easily network devices is key, and DHCP remains an important way for ensuring that devices can join networks and are set appropriately, even though it has been around for decades.
When IP addresses are issued manually, DHCP considerably decreases errors and can stretch IP addresses by limiting how long a device can keep a particular IP address.
DHCP stands for Dynamic Host Configuration Protocol.
Dynamic host configuration protocol (DHCP) is a network protocol used on IP networks in which a DHCP server assigns an IP address and other information to each host on the They need to be connected to the network in order to communicate with other endpoints effectively.
DHCP assigns the subnet mask, default gateway address, domain name server address, and other setup information in addition to the IP address. DHCP is specified as an Internet Engineering Task Force (IETF)-defined standard based on the BOOTP protocol in Request for Comments (RFC) 2131 and 2132.
DHCP makes managing IP addresses easier.
The basic reason for DHCP's existence is to make network IP address management easier. There can't be two hosts with the same IP address, and manually configuring them will almost certainly result in issues. Manually assigning IP numbers, even on small networks, can be perplexing, especially with mobile devices that require IP addresses on a non-permanent basis. Furthermore, most people lack the technical knowledge required to discover and assign an IP address on a computer. This process can be automated to make life easier for both users and network administrators.
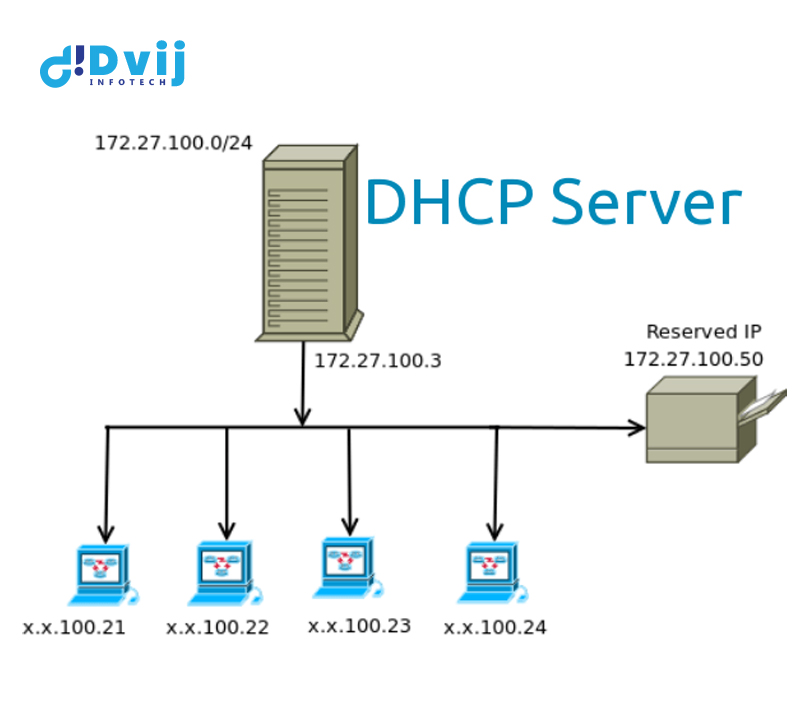
DHCP's Components
- It's critical to grasp all of the components of DHCP while working with it. The following is a list of who they are and what they do:
- A networked device that runs the DCHP service and stores IP addresses and related configuration information is referred to as a DHCP server. It's usually a server or a router, but it might be anything that serves as a host, such as an SD-WAN device.
- The endpoint that receives configuration information from a DHCP server is known as a DHCP client. It could be a PC, a mobile device, an IoT endpoint, or anything else that requires network connectivity. By default, most are set to accept DHCP information.
-
IP address pool:
The set of addresses that DHCP clients have access to. Addresses are usually distributed in order of importance, from the lowest to the highest.
- Subnets are segments of IP networks that can be divided into subnets. Subnets make networks easier to maintain.
-
Lease:
The amount of time a DHCP client retains IP address information.
The following is a list of who they are and what they do: A router or host that listens for client messages on a network and relays them to a designated server is known as a DHCP relay. The server then sends responses to the relay agent, who then passes them on to the client. Instead of having a server on each subnet, this can be used to centralize DHCP servers.
The advantages of DHCP servers. Aside from making maintenance easier, using a DHCP server has other advantages. These are some of them:
Customer Service in the Future: Data-Driven and Full of Opportunities
IP address setting must be precise:
It's easy to make a mistake when dealing with inputs like "192.168.159.3." Typographical errors are notoriously difficult to troubleshoot, and using a DHCP server reduces the possibility of this happening. Typographical errors are notoriously difficult to troubleshoot, and using a DHCP server reduces the possibility of this happening.
IP address conflicts are reduced:
because each connected device requires an IP address. However, each address can only be used once, and using the same address twice can cause a conflict, preventing one or both devices from connecting. When addresses are allocated manually, this can happen, especially if there are a high number of endpoints that only connect on a regular basis, such as mobile devices. Because DHCP is employed, each address is only used once.
DHCP automates IP address management:
Without IP address management, network administrators would have to assign and revoke addresses manually. It's practically impossible to comprehend when gadgets want network connection and when they leave, so keeping track of which device has which address might be a futile effort. This can be automated and centralized via DHCP, allowing network administrators to administer all locations from a single place.
Change management that works:
Changing addresses, scopes, or endpoints is a breeze when using DHCP. An organization, for example, might seek to switch its IP addressing scheme from one range to another. The updated information is configured in the DHCP server, and it will be propagated to the new endpoints. Similarly, if a network device is upgraded and replaced, it must be upgraded and replaced as well. It's not necessary to set up a network.
DHCP has security flaws.
The DHCP protocol does not require authentication, any client can rapidly join a network. As a result, it introduces a number of security problems, such as unauthorized servers disseminating inaccurate information to clients, unauthorized clients receiving IP addresses, and IP address depletion due to unauthorized or malevolent clients.
Because the client has no way of verifying a DHCP server's authenticity, rogue servers can be exploited to deliver erroneous network information. This can result in denial-of-service attacks or man-in-the-middle attacks, in which a phony server intercepts data for malevolent purposes. The DHCP server, on the other hand, has no way of verifying a client, thus it will give out IP address information to any device that requests it. A threat actor may set up a client to change its credentials on a regular basis and quickly exhaust all available IP addresses in the scope, preventing enterprise endpoints from connecting to the network.
Some of these concerns are addressed in the DHCP specification. Engineers can tag DHCP communications as they come on the network using the Relay Agent Information Option. This tag can be used to restrict network access. Authentication of DHCP messages is also possible, but key management can be difficult, which has slowed adoption. To secure DHCP, you can employ 802.1x authentication, also known as network access control (NAC). NAC is now supported by the majority of major network suppliers, and it is much easier to set up.